News
Security Researchers Find Nearly Dozen Holes in GE Ultrasound Machines
A line of ultrasound machines produced by GE HealthCare, the leading ultrasound OEM by market share, has been found to be susceptible to ransomware attacks and patient data compromise.
Researchers at IoT security firm Nozomi recently published a report identifying 11 vulnerabilities in GE's Vivid Ultrasound family of devices. "The impacts enabled by these flaws are manifold: from the implant of ransomware on the ultrasound machine to the access and manipulation of patient data stored on the vulnerable devices," the researchers wrote.
Nozomi focused its report on the Vivid T9 ultrasound device, which is designed primarily for cardiac ultrasound imaging. Each Vivid T9 device comprises a desktop running Windows 10 IoT; a native keyboard and trackpad; Common Service Desktop, a Web interface for performing administrative tasks; and EchoPac, the software used by clinicians to review ultrasound images.
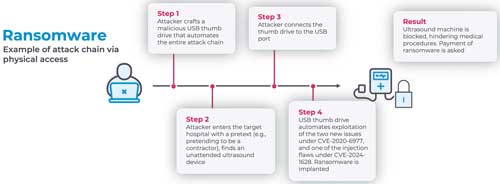
The flaws Nozomi found leverage all of these components, resulting in multiple avenues for attackers to perform arbitrary code execution with administrative privileges. Bad actors with physical access to a Vivid T9 device can execute attacks, either by directly interacting with it or by attaching a thumb drive that emulates the keyboard, but they can also execute attacks over the local network.
The attacks, Nozomi argued, can result in either ransomware or harm to patient data. In terms of ransomware, the researchers wrote:
[W]e successfully verified the ability to lock the Vivid T9 by means of a proof-of-concept ransomware. After physically accessing the device and removing all Windows security protections (which was possible due to the full privileges obtained), we were able to disrupt the device logic while simultaneously showing a picture on the screen asking for the payment of a ransom. ... A similar payload may also be executed against a doctor’s workstation running Echopac.
 [Click on image for larger view.]
Ransomware attack process. (Source: Nozomi)
[Click on image for larger view.]
Ransomware attack process. (Source: Nozomi)
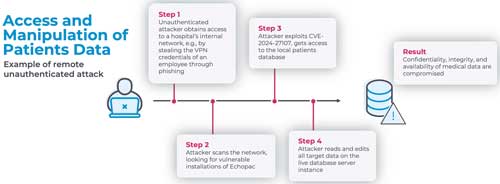
Regarding harm to patient data, Nozomi explained the attack method this way:
[H]aving achieved code execution with full privileges on a target system, nothing can stop an attacker from accessing and even manipulating all patient data stored on it. For instance, when considering Echopac, all patient data is stored in the companion SQL Anywhere. These databases can be easily accessed after exfiltrating and loading the file in a compatible client...or, even more simply, by sending SQL commands to the exposed network port.
 [Click on image for larger view.]
Patient data compromise attack process. (Source: Nozomi)
[Click on image for larger view.]
Patient data compromise attack process. (Source: Nozomi)
The following are the 11 vulnerabilities identified by Nozomi:
| CVE ID |
CWE |
CVSS v3.1 Base Score |
CVSS v3.1 Vector |
| CVE-2024-27107 |
Use of Hard-coded Credentials (CWE-798) |
9.6 |
CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H |
| CVE-2020-6977 |
Protection Mechanism Failure (CWE-693) |
8.4 |
CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| CVE-2024-1628 |
Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') (CWE-78) |
8.4 |
CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| CVE-2024-27110 |
Execution with Unnecessary Privileges (CWE-250) |
8.4 |
CVSS:3.1/AV:A/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H |
| CVE-2024-1630 |
Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') (CWE-22) |
7.7 |
CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N |
| CVE-2024-27109 |
Insufficiently Protected Credentials (CWE-522) |
7.6 |
CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H |
| CVE-2024-1486 |
Incorrect Permission Assignment for Critical Resource (CWE-732) |
7.4 |
CVSS:3.1/AV:L/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H |
| CVE-2024-27108 |
Incorrect Permission Assignment for Critical Resource (CWE-732) |
6.8 |
CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| CVE-2020-6977 |
Execution with Unnecessary Privileges (CWE-250) |
6.4 |
CVSS:3.1/AV:P/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H |
| CVE-2024-1629 |
Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') (CWE-22) |
6.2 |
CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N |
| CVE-2024-27106 |
Missing Encryption of Sensitive Data (CWE-311) |
5.7 |
CVSS:3.1/AV:A/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N |
GE has updated its product security portal with guidance for many of the above vulnerabilities, as well as a comprehensive lists of affected machines.
To prevent the attacks described, Nozomi encouraged organizations to avoid leaving Vivid ultrasound machines unattended "even for a short period of time," and to practice good network security hygiene -- for instance, by limiting network activity to only what's essential.
Specifically for machines with EchoPac installed, the researchers suggested "[blocking] incoming connections via firewall to SMB and 2638/tcp (SQL Anywhere DB server port) when the workstation is connected to an unprotected network."